
Each key value is entered as a 16-byte hexadecimal string with optional spaces between successive bytes, except when choosing the 3K3DES (three-key triple DES) encryption method, in which case the key has 24 bytes. The crypto methods 3K3DES and AES are only available for DESFire EV1. Note that AES is the recommended crypto method, as it complies with the internationally recognized security standards. 3K3DES is known to give technical problems with the OmniKey encoders and is NOT recommended.
By the default, the key specified in the key-value text boxes are the DESFire keys themselves. However, CardExchange Press offers the possibility to use diversified or randomized keys. Next to the crypto-method drop-down menu, a  button allows for choosing between these options.
button allows for choosing between these options.
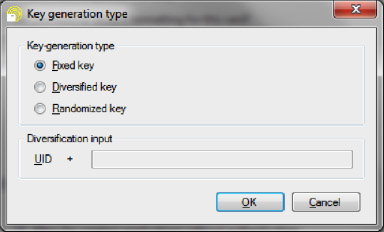
Diversified keys are a protocol in which the actual DESFire keys are different on all cards, thus offering an extra security layer. The actual keys can be calculated by using a master key and a diversification input. The diversification input contains the card’s UID, which ensures that the results of the calculations are different for every card. When diversified keys are enabled, CardExchange Press expects you to specify the diversification master key, rather than the DESFire key itself.
In case of diversified keys, it is necessary to specify the diversification input. The diversification input always starts with the DESFire UID and can be followed by any data the user desires (like the application AID and/or the key number). Note that key diversification has only been implemented for AES keys and follow the application note AN10922 published by NXP. In this document the byte 0x01 that precedes the diversification input is not considered part of the diversification input, but it is important to realize that CardExchange Press does actually add this byte to construct the CMAC input parameter D.
When randomized keys are enabled, CardExchange Press will use a random key value rather than the one you typed. This option should only be used for new keys, as the result will never coincide with an existing key, and you should only use it if you are sure that you never want to use that key again. It is a way to lock the possibility to make certain changes to the card, in addition to the key settings.
Using the MIFARE® SAM AV2 secure application module is another case in which you will not supply the real DESFire keys either. Instead, you will need to use the key-value box to supply encoded instructions about how to authenticate with the SAM. You have to specify the following information:
•Byte 0 contains either the SAM key number or the application key number.
•Byte 1 contains the key version.
•Byte 2 contains the authentication mode, which can have the following values (other options are not supported by the DESFire-definition wizard):
o0 when the key is not diversified and byte 0 contains the SAM key number.
o2 when the key is not diversified and byte 0 contains the application key number.
Key diversification can be used in combination with the SAM AV2 module. CardExchange Press will always use the MIFARE® SAM AV2 mode diversification and set the corresponding bits of the authentication mode automatically.
